Finest approaches to secure your web application
Table Of Contents
Introduction
Web application security is an important aspect of web application development that is sometimes disregarded. It’s very understandable.
Web application security threats are frequently neglected or undervalued due to the complexity of code development, app maintenance, and visual design.
Even yet, if you expect to make money from your app, web application security should be a top focus. Fortunately, there are several simple techniques to increase web app security. Many firms shifted to working remotely in virtualized corporate systems in 2020, and application security teams had to adjust to a shift in utilization and an increasing number of difficulties.
Web apps are now an essential part of business and daily life. Businesses and people may simplify and get more things done with fewer resources by adopting web applications, attaining goals much quicker than they did before.
What is meant by the security of web applications?
A web application is a piece of software that runs on your web application (rather than on specific devices as standard desktop software does). Web application security refers to everything that has to do with safeguarding your web applications, resources, and infrastructure against cyber-attacks and dangers. This includes everything from your guidelines and practices to the technologies you use to prevent attackers from exploiting vulnerabilities.
We design complicated online applications in the age of cloud technology that can store digital versions of your complete life in one spot. As a result, web application security, both server-side and client-side, is no longer a choice but a must.
What exactly do you mean by Web Applications (Web-apps)?
A Web application (Web app) is a computer application program that is maintained on a distant server and accessed via the Internet using a browsing interface. Web services, by design, are Web apps, and many, but not all, websites incorporate Web apps. A Web app is any element of a website that provides functionality for the visitor or client.
Web apps can be built for a wide range of purposes and utilized by anybody, from businesses to individuals, for a number of reasons. Email account, online spreadsheets, and e-commerce stores are examples of commonly used Web apps. Some Web apps are only accessible through a certain browser, nonetheless, the majority are reachable through any browser. As web applications are available over the internet, they do not require external downloading.
A web app requires a Web server, an application server, and a database to run. Client queries are handled by web browsers, while the application server accomplishes the specified operation. Any type of information can be stored in a database.
Web apps have quick development phases and may be built by small groups of developers. JavaScript, Reactjs, and CSS are used to create the majority of Web applications (CSS). These languages are commonly used in client-side programming to assist develop a software’s front-end. To develop the code snippets that a Web app will employ, server-side programming is used. In server-side programming, languages like Python, Java, and Ruby are frequently utilized.
An Example!
BlackBerry Limited is a cybersecurity firm based in Canada that focuses on corporate key event management solutions, endpoint protection, and safeguarding the Internet of Things by employing artificial intelligence and machine learning to combat cyberthreats.
Its technologies are used to resist phishing attacks and data breaches by a variety of corporations, automobile manufacturers, and governmental organizations. BlackBerry Cylance‘s increasingly digital cyber-security solutions are among them.
Best security approaches for your web application
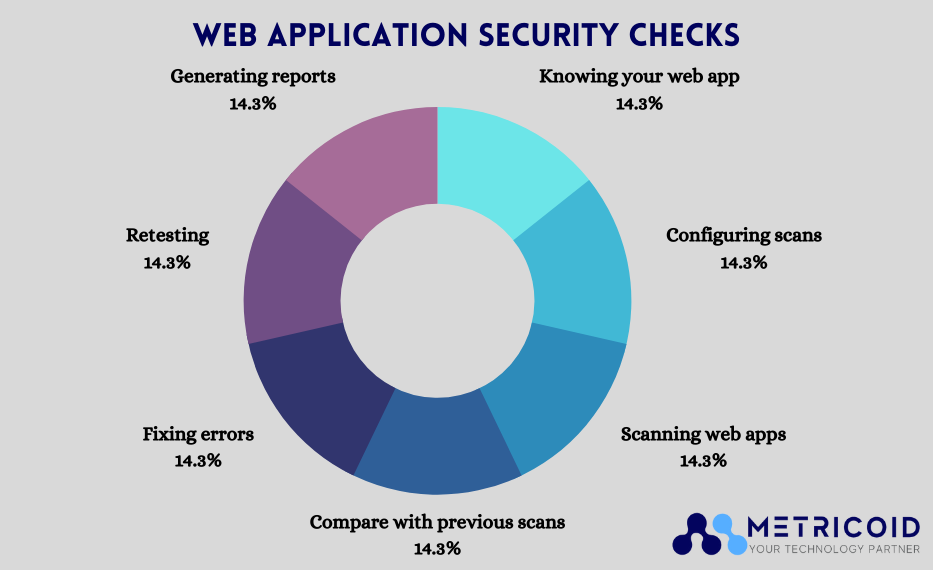
Web application security is a dynamic topic of cybersecurity and it can be challenging to keep track of evolving technology, security flaws, and attack vectors. Let’s look at a few web application security best practices that might help you keep your security threats under control.
-
Static Application Security Testing (SAST)
Static Application Security Testing (SAST) solutions look for vulnerabilities and security concerns in your source code. Code scanning is used in many online applications at various stages of development, most notably when committing new code to the repository and during a build.
Because SAST is usually rule-based and scan results often contain false positives, you’ll need to thoroughly examine and analyze the data to find true security vulnerabilities.
-
Check your website for flaws on a regular basis
To remain ahead of web app security, security checks and scans should be performed on a frequent basis. Security checks on your web pages should be performed at least weekly.
You must also analyze your application after every modification you make. It’s worth mentioning that even the best security detectors won’t be able to identify everything. Malware is always designed to be undetectable to scanners, and scanners are either intuitive or pattern-based.
Some scanners are better at detecting malware, while others struggle with false positives, and others just don’t operate at all. You should continue to educate yourself on security issues and vulnerabilities.
-
Dynamic Application Security Testing (DAST)
DAST (Dynamic Application Security Testing) is a method of finding vulnerabilities in code that has been deployed or is now operating. It can be done manually or automatically with the help of appropriate technologies.
Manual testing entails using applications such as Axway, Fiddler, and Postman to interact with application APIs. In order to find vulnerabilities, automation DAST programs send a huge number of queries to application code, including unanticipated and hostile inputs. It examines the data and discovers security flaws.
-
Everybody should be involved in security procedures
Some companies still assume that security is something that should be handled by a dedicated staff. Such a strategy is no longer viable in today’s corporate environment:
- Because of the growing cybersecurity skills gap, security teams are struggling to keep up with corporate development.
- In the development phase, a dedicated security staff becomes a constraint.
- There are more challenges for the security team to deal with if security is reactive rather than proactive.
-
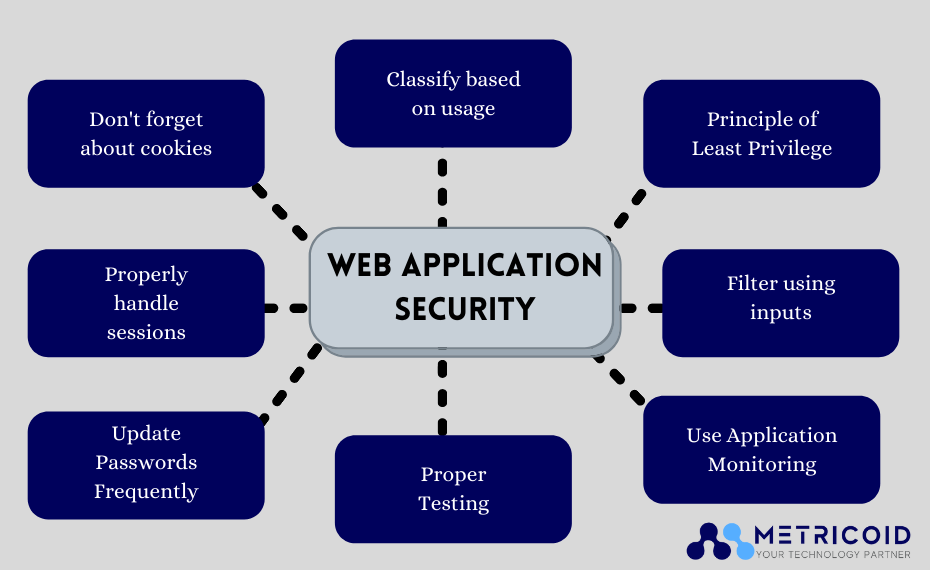
Make a list of all of your web-based applications
Even if you think your firm is well-organized, you presumably don’t have a clear grasp of the programs it uses on a regular basis. In reality, most businesses have a large number of malicious programs operating at any given moment and are unaware of them until stuff goes wrong. Without understanding which applications your firm employs, you can’t expect to maintain efficient web application security.
How many are in total? What city are they in? Performing quite an inventory is a large task that will most likely take some time to accomplish. Make a note of the purpose of each application as you go through it. When all is said and done, there will almost certainly be numerous apps that are either superfluous or utterly obsolete.
-
Managing exceptions
Exceptions are a feature of web application security that is sometimes disregarded. Exceptions or faults that display long stack trails to the user are prevalent – this knowledge is immensely helpful to attackers. You must never show a user anything other than a warning message explaining what did go wrong and how they may fix it.
Make sure your webpage is prepared for both pleasant as well as unpleasant user scenarios. Predict all potential mistakes and respond with appropriate exceptions. As a result, attackers will be unable to take advantage of edge circumstances to trigger unexpected behavior.
-
Categorize and divide your web applications
After you’ve completed your evaluation of the current web applications, the very next reasonable step is to prioritize them. You may not believe it right now, but your to-do list is going to be quite big. It will be difficult to make any significant effort until you prioritize which applications to concentrate on initially.
Externally accessible applications that include client data are considered essential. These are the programs that should be handled first, as they are the ones that attackers are most likely to hit and compromise. Believe that positive might be internal or external, and they can include sensitive data. Normal applications are exposed to significantly less radiation, but they should be included in future tests.
-
Vulnerable points must be your top priority
It’s just not possible, or even worthwhile, to eliminate all vulnerabilities from all web apps. Even after prioritizing your applications based on their relevance, testing them all will take a long time. You will conserve a huge amount of time and get through the job a lot faster if you limit yourselves to only screening for the most dangerous vulnerabilities.
When it comes to deciding which vulnerabilities to focus on, it all comes down to the programs you’re utilizing. Basic security procedures should be deployed, but application-specific vulnerabilities should be studied and analyzed.
Please remember that as the testing progresses, you may discover that you have ignored some flaws. Don’t be frightened to put your evaluation on hold while you reorganize and work on other issues. Finally, keep in mind that this task will be a lot easier in the future because you are starting afresh currently and will not be later.
Conclusion
As you can see, implementing web application security best practices is a collaborative effort if you’re part of an organization. There are clearly practical steps you can take to increase the security of your app rapidly and easily. However, when applications expand in size, they become increasingly difficult to manage in terms of security. Using the web application security best practices indicated in the list above, you can assist ensure that your applications are secure to use for everybody.
Metricoid Technology Solutions, one of the top companies that can provide a wide range of security services, including building SaaS (software-as-a-service) applications and thorough digital alternatives for a variety of industries and applications, is a great place to start if you’re having to look for a great tech partner for your startup, assisting in security services. From application design and implementation to testing, debugging, timely maintenance, and methodical integration with other apps, everything here is taken care of in Metricoid’s development phase, which is provided at a cheap cost.






